Don't Put off Building a Comprehensive Incident Response Plan

Don't Put off Building a Comprehensive Incident Response Plan
This article defines an incident response plan (IRP) and why it’s critical for businesses of all sizes, the components of an IRP (the incidents it should cover, helpful forms to include for documentation, and the incident response lifecycle), and ends with 4 tips for creating an effective IRP.
You may have heard the saying, "Hope for the best, but prepare for the worst." This phrase is more relevant than ever, especially regarding cybersecurity. Most businesses depend on technology daily to streamline operations and improve efficiency, but what happens when technology fails, and operations are disrupted?
The reality is that cybersecurity incidents are entirely out of our control, and nothing we do can ensure we're 100% safe. Businesses of every size are at risk and should have a plan for when (not if) they experience a cybersecurity incident.
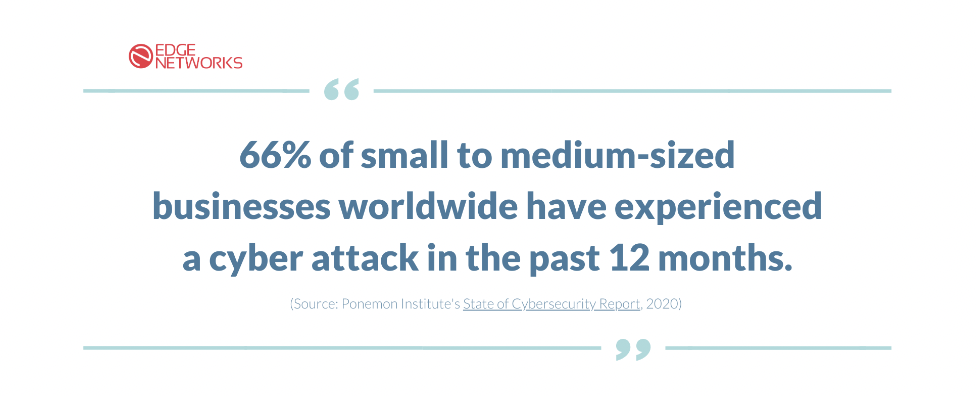
According to Ponemon Institute's State of Cybersecurity Report, 66% of small to medium-sized businesses worldwide have experienced a cyber attack in the past 12 months. An incident response plan can help businesses of all sizes protect their sensitive information and minimize the impact on operations, finances, and reputation.
Connect with top cybersecurity companies on The Manifest.
This article will define an incident response plan, the types of incidents it should cover, and the critical components of an IRP. It will also offer practical tips on developing and implementing a plan that fits your organization.
What is an Incident Response Plan, and Why Does My Business Need One?
An incident response plan (IRP) is critical to a comprehensive cybersecurity strategy for many reasons. It helps businesses of all sizes prepare for a potential crisis, so they know how to identify it and where to turn for the next steps by including the procedures needed to mitigate any incident that should occur. IRPs should be reviewed regularly and updated to address emerging threats and changes in a business' infrastructure.
What Types of Incidents Does an IRP Cover?
An incident response plan should cover any incident that impacts an organization's operations, data, or information technology infrastructure. This includes the following:
- Cyber-attacks
- Data breaches
- Physical security breaches (theft, vandalism, sabotage, etc.)
- Natural disasters
- Power outages
- Equipment failures, and other emergencies.
Having a well-thought-out IRP can be the difference between survival and catastrophe. It can help minimize damage, restore normal operations, reduce recovery time, and prevent similar incidents.
What Does an Incident Response Plan Entail?
Roles and Responsibilities
A section outlining employee roles and responsibilities is critical for better organization and communication during an incident. This section should include employee names, contact information, and incident-specific tasks. This section should establish the Security Incident Response Team (SIRT) with clearly defined roles and responsibilities for team members, so they know who is responsible for responding to and managing specific aspects of security incidents.
This phase should also include regular security awareness training for all employees and testing exercises to ensure the team knows what to look out for and can respond to a security incident effectively.
Some IRPs split their SIRT into teams. The management team comprises at least one employee that makes financial and staffing decisions, provides staff support, and activates the plan. The coordination team notifies the response team, maintains the incident status, informs people affected by the incident, and conducts the follow-up. The response team determines the extent of damage done, recommends a course of action, and carries out the containment, eradication, recovery, and follow-up phase processes.
Incident Handling Forms
All IRPs should contain incident handling forms to ensure the incident is well-documented. This component is essential for effective incident response and future prevention.
Some forms that should be included in an incident response plan are:
- Incident Identification Form: This form is used once an incident is discovered. It includes, in detail, the description of the incident, how the incident was detected, potential impacts (such as type of data and amount breached/lost, number of information systems and services impacted, etc.), security controls in place, outside organizations affected by the incident, the severity level, and more.
- Incident Containment Form: This form documents what is being done to contain the incident, such as disabling access to data or services and backing up information systems.
- Incident Eradication Form: The incident eradication form is used to dive into specifics of impacted information systems.
- Incident Follow-Up Form: The purpose of this form is to reflect on the incident and touch on topics such as time spent responding to the incident, costs (direct and indirect) of the incident, insight into how the company responded to the incident and areas of improvement, and more.
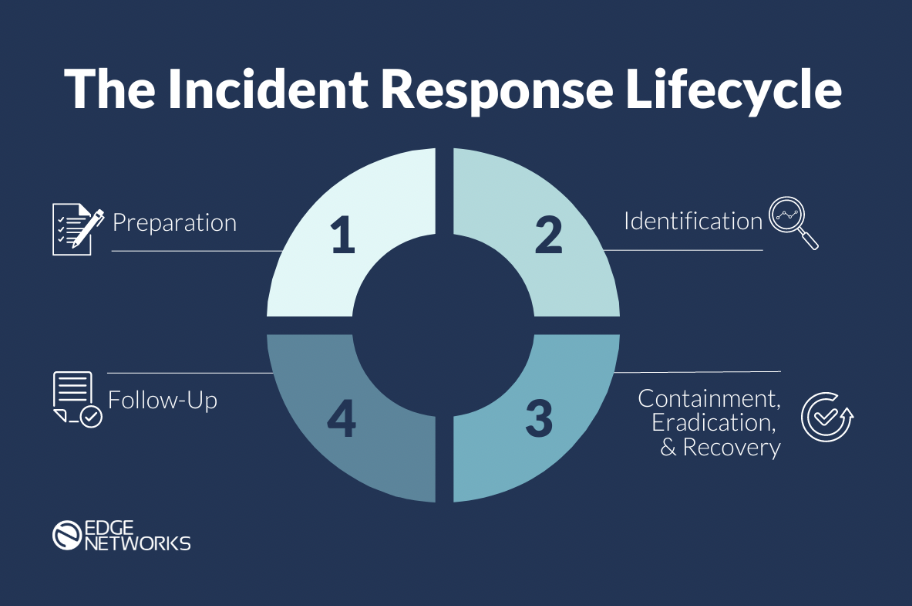
Incident Response Lifecycle
The incident response lifecycle is a framework for managing and responding to a cybersecurity incident. It consists of six phases, each with its action items and objectives, designed to help organizations prepare for, identify, contain, eradicate, and recover from a security incident.
The six phases are as follows:
- Preparation Phase: This phase should be completed before an incident impacts a company. It's the phase where an incident response plan is created, and procedures are developed and tested. It also involves establishing a Security Incident Response Team (SIRT).
- Identification Phase: In this phase, the incident response team identifies and assesses potential security incidents by monitoring network activity, logs, and other data sources to identify any potential incidents or suspicious activity quickly. If an incident has occurred, an Incident Coordinator on the team would determine its type and severity level and document the facts in a Security Incident Identification Form.
- Containment Phase: Once an incident has been identified, the focus shifts to containing the threat to prevent it from spreading further. This may involve isolating affected systems, blocking network traffic, backing up impacted information systems, disabling access to data or services, and changing all authentication credentials that may have been compromised during the incident. At this stage, if it is determined that a security incident has occurred, the SIRT management team should notify all people affected about the incident (such as information system owners and administrators, management, and third-party organizations who use the company's services or data).
- Eradication Phase: The eradication phase aims to eliminate the threat from affected systems and networks and mitigate the vulnerability that led to the incident. This may involve removing malware, applying patches or updates, performing vulnerability tests, improving defenses, or restoring affected systems from backups.
- Recovery Phase: This phase is focused on recovering all impacted data and services and returning to full operational status. This may involve repairing or rebuilding systems, reporting data breaches, monitoring data and services, and notifying all those affected when data and services are back to being available and functional.
- Follow-Up Phase: The focus of the follow-up phase is to identify what was learned from the incident, create a summarized document of the incident, analyze responses, and produce a follow-up report. Any employee involved should share their feedback on the incident response and provide any recommendations they have to improve the plan for future incidents.
4 Tips for Creating an Effective Incident Response Plan
Here are a few tips on getting started on your incident response plan:
1. Use a Template
One of the best ways to get started with an incident response plan is to download a free template from a reputable source. Doing this can save you time, provide best practices, and ensure all your bases are covered. This template should act as your foundation, which you can build off and edit as you go. Make sure the template covers the essential components listed above to make your job easier.
Download a free, comprehensive Incident Response Plan template here.
2. Hire a Cybersecurity Consultant
A cybersecurity consultant can help you assess your organization's security risks and develop an incident response plan tailored to your business’s specific needs. No matter how comprehensive an Incident Response Plan is, it generally requires someone technical trained in incident response to know how to properly contain the damage.
3. Consult with your IT department or IT Service Provider
Your IT department or IT service provider may have experience with incident response planning and can provide guidance on creating a plan that aligns with your organization's IT infrastructure.
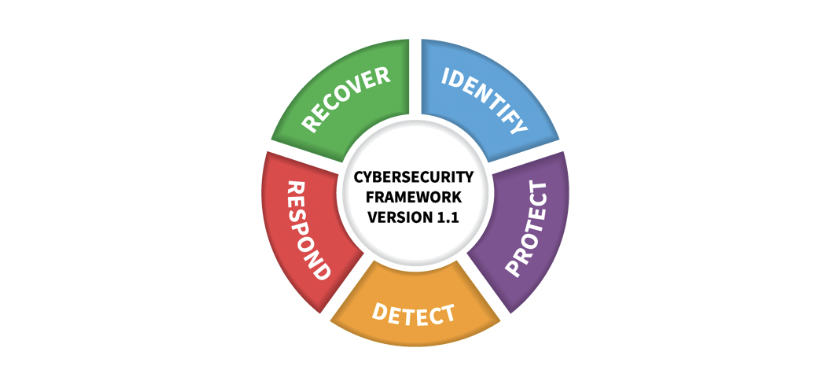
Source: National Institute of Standards and Technology
4. Follow Industry Standards
Industry standards such as the NIST Cybersecurity Framework or ISO 27001 provide guidance on incident response planning. Following these standards can ensure that your incident response plan aligns with best practices in your industry.
Creating an Effective Incident Response Plan is Crucial for Protection
Creating a comprehensive incident response plan is critical for every business that values its reputation, customer trust, and overall cybersecurity. An IRP is an ongoing process, and you shouldn't be afraid to update and improve your plan as you go along. With a bit of effort and commitment, your business can be well-prepared to handle any incident that comes your way.
Find and decide on the right cybersecurity firm to help your business on The Manifest.
